
How Identity.com Helps Businesses Meet Regulatory Compliance
Why Compliance Has Become a Business Risk, Not Just a Legal Requirement Compliance now touches far more than legal checklists

Why Compliance Has Become a Business Risk, Not Just a Legal Requirement Compliance now touches far more than legal checklists
Key Takeaways: The legality of training AI on copyrighted work remains unresolved, leaving creators and tech companies operating in a

Key Takeaways: Media Authenticity ensures that content is credible, reliable, and trustworthy, allowing audiences to make informed decisions and engage

Key Takeaways: A Digital ID is an electronic representation of an individual’s identity used for online verification. It allows individuals

Key Takeaways: Selective disclosure is the process of sharing only the information necessary for a specific purpose while keeping other

Key Takeaways: Digital likeness is a person’s image, voice, or other identifiable traits when represented online or through technology. With
Key Takeaways: Liveness detection is a biometric identity verification method used to confirm that a real, live person is present

Key Takeaways: Biometrics now function as credentials for many systems, but they cannot be reset. When exposed, the risk does
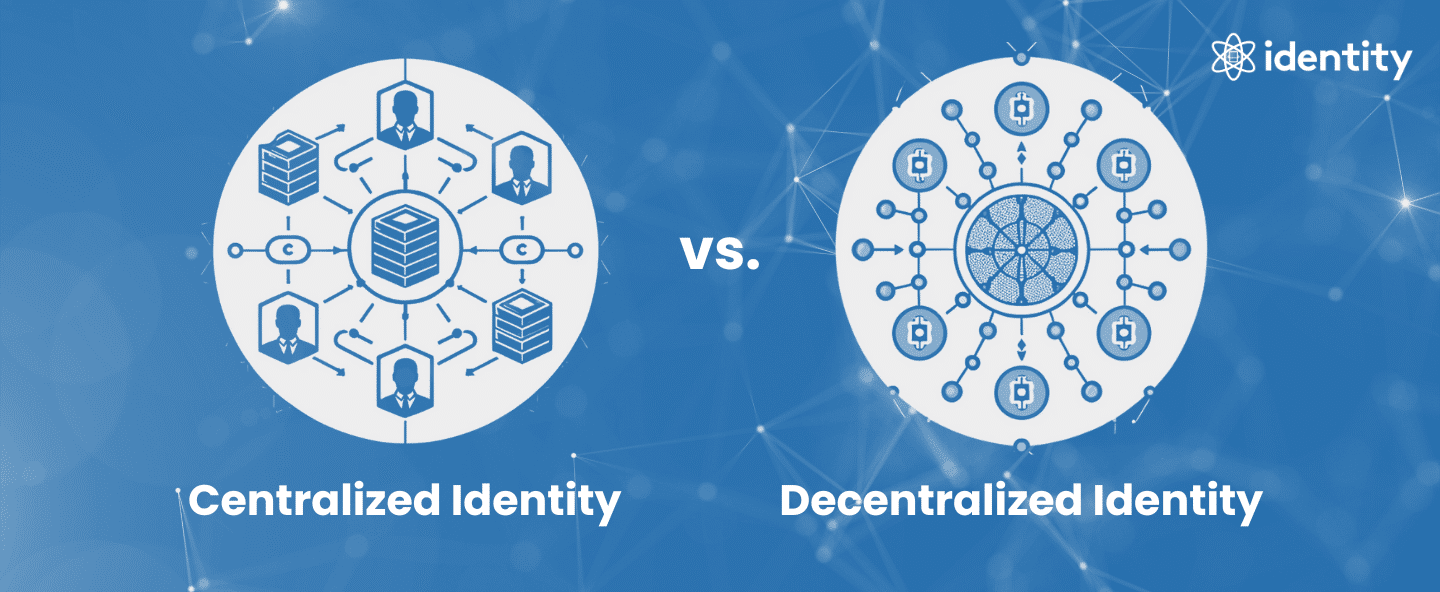
The rising popularity and market value of decentralized identity signal a significant shift in the landscape of identity management. For