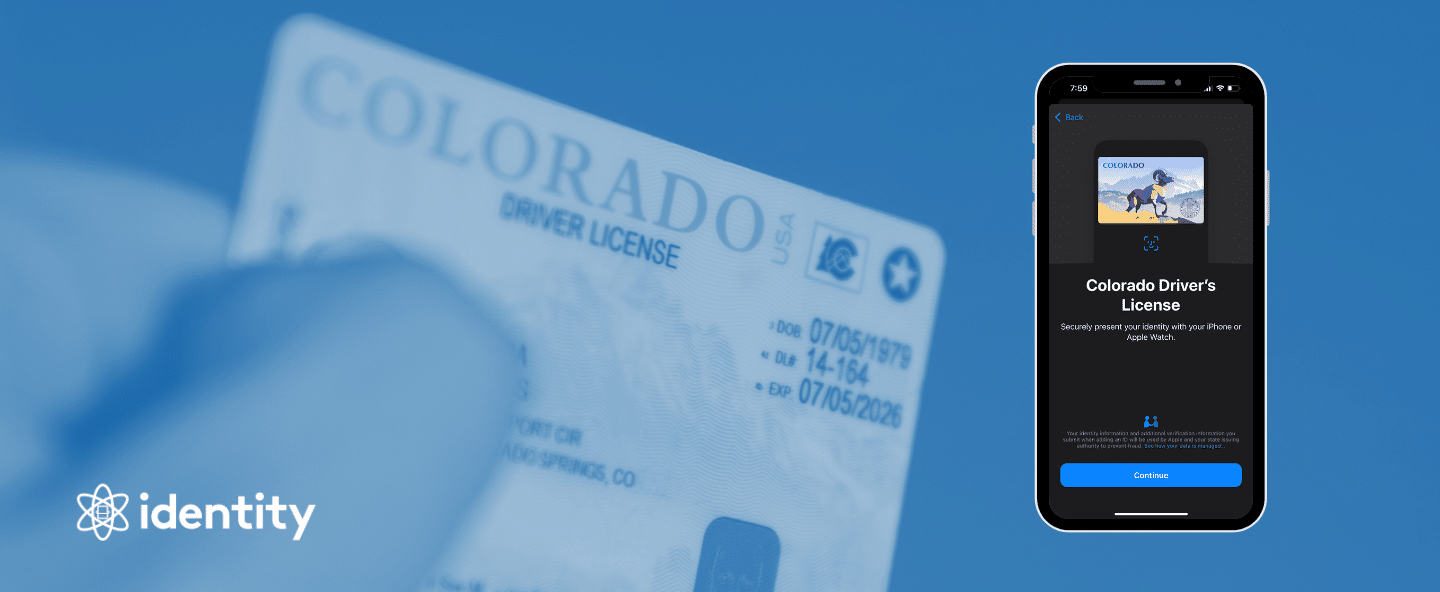
How Mobile Driver’s Licenses (mDLs) Enhance Identity Verification
Key Takeaways: Mobile Driver’s Licenses (mDLs) are digital driver’s licenses stored securely on a smartphone, offering a modern alternative to

Key Takeaways: Mobile Driver’s Licenses (mDLs) are digital driver’s licenses stored securely on a smartphone, offering a modern alternative to

Key Takeaways: Behavioral biometrics verify identity continuously based on how people interact with devices. They provide an invisible layer of

Key Takeaways: Self-sovereign identity (SSI) is a digital identity model that gives individuals full control and ownership over their personal

Key Takeaways: More people are turning to VPNs because new age-verification steps feel intrusive, inconvenient, or unclear about how personal

Key Takeaways: The positive side of deepfakes and AI lies in how they’re transforming industries such as film, education, and

Key Takeaways: Authentication verifies a user’s identity, while authorization determines what resources that verified user can access. Both authentication and

Key Takeaways: Account takeovers happen when attackers gain unauthorized access to someone’s account using stolen credentials, phishing, or weaknesses in

The World Wide Web Consortium (W3C) is the unsung hero behind today’s seamless and interconnected digital world. Founded in 1994

Key Takeaways: A digital certificate is an electronic document that verifies the ownership of a public key in cryptographic systems.